- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Black Hat: The Black Hat Briefings have become the biggest and the most important security conference series in the world by sticking to our core value: serving the information security community by delivering timely, actionable security information in a friendly, vendor-neutral environment.
- Hack Forums: Emphasis on white hat, with categories for hacking, coding and computer security.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- Phrack Magazine: Digital hacking magazine.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- Offensive Security Training: Developers of Kali Linux and Exploit DB, and the creators of the Metasploit Unleashed and Penetration Testing with Kali Linux course.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Makezine: Magazine that celebrates your right to tweak, hack, and bend any technology to your own will.
Jun 30, 2020
Top 17 Best Websites To Learn Hacking 2018
¿QUÉ PASÓ CON LOS RESTOS DE HITLER? (Vídeo De La BBC)
More information
- Viaje 420
- Viaje Skull And Bones Cigars For Sale
- Viaje 4 Patas
- Curiosidades 11 De Septiembre
- Viaje Barato
- Viaje Que Significa
- Viaje De Chihiro
- Lifestyle Z Square Kanpur
- Curiosidades Wwe
- Lifestyle 600 System
- Curiosidades Forrest Gump
- Viaje Inmovil
- Lifestyle 50 Bose
- Viaje Republica Dominicana
- Curiosidades Windows
- Curiosidades Con Mike Edad
- Curiosidades 3Ds
- Curiosidades Puerto Rico
- Lifestyle Near Me Offers
- Lifestyle Management
- What Viajar Mean In Spanish
- Curiosidades Lgbt
- Lifestyle 4 Living
- Curiosidades In English
- Viaje Y Turismo
- Viaje Farmhand Andre
- Curiosidades Você Sabia
- Curiosidades 8 Mile
- Viaje Y Turismo
- Curiosidades Animais
- For Lifestyle Collection
- Curiosidades Batman Vs Superman
- Lifestyle Markets
- Curiosidades Con Mike Libro
- Viaje Que Es
- Viaje Por Europa
- Viajar Vs Ca Case Digest
- Lifestyle Entrepreneur
- Lifestyle Wireless
- Curiosidades 9
- Curiosidades 80S
- How Often Do Lifestyle Condoms Break
- Who You Are Curiosidades
- Lifestyle 360 App
- Viaje Misionero De Pablo
- Viaje 3
- Lifestyle Logo
- Curiosidades Juego De Tronos
- Lifestyle 74
- Curiosidades Keanu Reeves
- Lifestyle Ultra Sensitive Review
- Curiosidades Y Algo Mas
- Lifestyle 550
- Lifestyle 6X4Ft Greenhouse With Base
- Lifestyle Centre
- Lifestyle Video Ideas
- Lifestyle Elliptical
- Lifestyle Vs Diet
- Are Lifestyle Diseases Preventable
- 033 Lifestyle 1000 Hills
- Curiosidades Himym
- Viaje Kenia Y Zanzibar Precio
- Curiosidades 9/11
- Viaje Past Tense
- Lifestyle Equipment
- Curiosidades Plants Vs Zombies 2
- Curiosidades 13 Reason Why
- Viaje Ultimo Minuto
- What Does Curiosidades Mean In Spanish
- Viaje Virtual A Paris
- Curiosidades Instagram
- Viaje Hacia El Mar
- Lifestyle Nails
- Viaje Platino Perfecto
- Viaje Kenia Tanzania Y Zanzibar
- Viaje Koino Yokan
- Lifestyle Returns
- Curiosidades 6 De Agosto
- How Lifestyle Affects Circulatory And Respiratory System
- Lifestyle 8321
- Viaje A Marte
- Viaje Hamaki
- Curiosidades Tecnologicas
- Curiosidades Zootropolis
- Viaje 6 Dias Europa
- Viaje Super Shot
- Lifestyle 011
- Viajes Or El Mundo
- Another Word For Viaje
- Viaje Uber
- Curiosidades Wwe
- Viaje 7 Dias Marruecos
- French Word For Viaje
- Lifestyle 48 Series Iv
- Curiosidades The Office
- Curiosidades Ucrania
- Lifestyle 38
- Is Viaje A Noun
- Curiosidades Meaning
- Curiosidades Sobre 007
- Who Lifestyle Guidelines
- Lifestyle Trichy
- Curiosidades Mundo Animal
- Viaje Inmovil
- Why Don'T We Curiosidades
- Curiosidades Historia
- Viaje Vs Recorrido
- Will Witon Viaje A Las Estrellas
- Lifestyle Extra Sling
- Curiosidades Koalas
- Lifestyle X
- Lifestyle 535 Series Iii
- Curiosidades Benjamin Lacombe
- Curiosidades Libros
- Viaje Seguro
- Lifestyle Rentals
- Viaje Zombie Farmer Bill Hatchet
- Lifestyle Zoom
- Curiosidades Medicas
- Curiosidades Walking Dead
- Curiosidades 5 De Mayo
- Curiosidades Japon
- Lifestyle Of Bill Gates
- Curiosidades Xiaomi Redmi Note 8 Pro
- How Many Lifestyle Apps Are There
- Where Can Lifestyle Vouchers Be Used
- Viaje Hamaki Omakase
- Viaje In English
- Viaje 3 De La Tierra Ala Luna
- Curiosidades 50 Sombras De Grey
- Lifestyle 365
- Curiosidades Resident Evil
- Curiosidades Que Ninguém Sabia
- How To Say Viaje In English
- Why Nirmal Lifestyle Mulund Closed
- Curiosidades Zelda Breath Of The Wild
- Viaje 7 Dias Nueva York
- Lifestyle Wake
- Lifestyle 011
- Viaje De Chicas
- Curiosidades Benjamin Lacombe
- Why Healthy Lifestyle Is Important
- Fecha Viaje To English
- Curiosidades Sobre O Corpo Humano
- Lifestyle Of The Rich And Famous Lyrics
- Lifecycle 9500Hr
- When Does Lifestyle Sale Start
- Viaje Craft Series
- Viaje Bruce Banner Cigar Review
- Viaje En El Tiempo Pelicula
- Lifestyle 0
- Curiosidades Para Niños
- Viaje Por Viajes
- Spanish Translation For Viaje
- Viaje En El Tiempo
- Viaje Tailandia
- Lifestyle Zero Review
- Viaje Verde Letra
- 4 To Viaje De Colon
- Curiosidades Que No Sabias
- Lifestyle Network
Jun 28, 2020
re: Cheap Facebook Traffic
hi
a-camping-we-will-go.htmlnoreply
here it is, social website traffic:
http://www.mgdots.co/detail.php?id=113
Full details attached
Regards
Annita Aumick �
Unsubscribe option is available on the footer of our website
a-camping-we-will-go.htmlnoreply
here it is, social website traffic:
http://www.mgdots.co/detail.php?id=113
Full details attached
Regards
Annita Aumick �
Unsubscribe option is available on the footer of our website
Jun 16, 2020
re: Rank 1st in google with Content Marketing Strategy
hi
Get your business to the next level with a solid Content Marketing strategy
http://www.str8-creative.io/product/content-marketing/
Regards
Tera Riegel �
Unsubscribe option is available on the footer of our website
Get your business to the next level with a solid Content Marketing strategy
http://www.str8-creative.io/product/content-marketing/
Regards
Tera Riegel �
Unsubscribe option is available on the footer of our website
Jun 11, 2020
Stegcloak - Hide Secrets With Invisible Characters In Plain Text Securely Using Passwords
StegCloak is a pure JavaScript steganography module designed in functional programming style, to hide secrets inside text by compressing and encrypting with Zero Width Characters. It can be used to safely watermark strings, invisible scripts on webpages, texts on social media or for any other covert communication. Completely invisible!. See how it works in-depth here
Features
- Protect your invisible secret using passwords and HMAC integrity
- Cryptographically secure by encrypting the invisible secret using AES-256-CTR.
- Uses 7 Invisible characters in unicode characters that works everywhere in the web.
Including the most important ones Tweets, Gmail, Whatsapp, Telegram, Instagram, Facebook etc. - Maximum Compression to reduce the payload (LZ, Huffman).
- Completely invisible, uses Zero Width Characters instead of white spaces or tabs.
- Super fast! Hides the Wikipedia page-source for steganography (800 lines and 205362 characters) within a covertext of 3 words in under one second.
- Written in pure functional style.
- Usage - Available as an API module, a CLI and also a Web Interface (optimized with web workers).
Installing
Using npm,
$ npm install -g stegcloak$ npm install stegcloakHow it works
CLI Usage
Hide
$ stegcloak hide hide [options] [secret] [cover]
-f, --file <file> Extract input from file
-n, --nocrypt If you don't need encryption (default: false)
-i, --integrity If additional security of preventing tampering is needed (default: false)
-o, --output <output> Stream the results to an output file
-h, --help display help for command
Reveal
$ stegcloak reveal reveal [data]
-f, --file <file> Extract input from file
-cp, --clip Copy Data directly from clipboard
-o, --output <output> Stream the secret to an output file
-h, --help display help for commandAPI Usage
const StegCloak = require('stegcloak');
const stegcloak = new StegCloak(true, false); // Initializes with encryption true and hmac false for hiding
// These arguments are used only during hide
// Can be changed later by switching boolean flags for stegcloak.encrypt and stegcloak.integrityWhat's HMAC and do I need it?
HMAC is an additional fingerprint security step taken towards tampering of texts and to verify if the message received was actually sent by the intended sender. If the data is sent through WhatsApp, Messenger or any social media platform, this is already taken care of! However, if you are using StegCloak in your program to safely transmit and retrieve, this option can be enabled and StegCloak takes care of it.
Hide
stegcloak.hide(secret,password,cover) -> stringconst magic = stegcloak.hide("Voldemort is back", "mischief managed", "The WiFi's not working here!");
// Uses stegcloak.encrypt and stegcloak.integrity booleans for obfuscation
console.log(magic); // The WiFi's not working here!Reveal
stegcloak.reveal(data, password) -> stringconst secret = stegcloak.reveal(magic, "mischief managed");
// Automatically detects if encryption or integrity checks were done during hide and acts accordingly
console.log(secret); // Voldemort is backImportant
Stegcloak does'nt solve the alice-bob-warden problem, its powerful only when people are not looking for it and it helps you to achieve that really well given its invisible properties around the web! It could be safely used for watermarking in forums, invisible tweets,irc chats,social media etc. Please don't use it when you know there's someone who is actively sniffing your data looking at the unicode characters through a data analysis tool, in that case even though the secret encoded cannot be deciphered the fact lies that the warden ( Middle-man ) now knows some secret communication took place, cause he would have noticed an unusual amount of special invisible characters.
Resources
The following papers were referred to for insight and understanding of using Zero Width Characters in steganography.
- Milad Taleby Ahvanooey, Qianmu Li , Jun Hou, Ahmed Raza Rajput and Chen Yini
Modern Text Hiding, Text Steganalysis, and Applications: A Comparative Analysis- Taleby Ahvanooey, Milad & Li, Qianmu & Hou, Jun & Dana Mazraeh, Hassan & Zhang, Jing.
AITSteg: An Innovative Text Steganography Technique for Hidden Transmission of Text Message via Social Media.
IEEE AccessAcknowledgements
The StegCloak logo was designed by Smashicons.
via KitPloit
This article is the property of Tenochtitlan Offensive Security. Verlo Completo --> https://tenochtitlan-sec.blogspot.com
Related articles
Collection Of Pcap Files From Malware Analysis

Update: Feb 19. 2015
We have been adding pcaps to the collection so remember to check out the folder ( Pcap collection) for the recent pcaps.
I had a project to test some malicious and exploit pcaps and collected a lot of them (almost 1000) from various public sources. You can see them in the PUBLIC folder. The credits go to the authors of the pcaps listed in the name of each file. Please visit their blogs and sites to see more information about the pcaps, see their recent posts, and send them thanks. The public pcaps have no passwords on them.
Update:Dec 13. 2014
Despite rare updates of this post, we have been adding pcaps to the collection so remember to check out the folder ( Pcap collection (New link)) for the recent pcaps!
Update:Dec 31. 2013 - added new pcaps
I did some spring cleaning yesterday and came up with these malware and exploit pcaps. Such pcaps are very useful for IDS and signature testing and development, general education, and malware identification. While there are some online public sandboxes offering pcaps for download like Cuckoo or Anubis but looking for them is a tedious task and you cannot be totally sure the pcap is for the malware family supposedly analysed - in other words, if the sandbox says it is Zeus does not necessarily mean that it is.
I found some good pcap repositories here (http://www.netresec.com/?page=PcapFiles) but there are very few pcaps from malware.
These are from identified and verified (to the best of my knowledge and belief - email me if you find errors) malware samples.
All of them show the first stage with the initial callback and most have the DNS requests as well. A few pcaps show extended malware runs (e.g. purplehaze pcap is over 500mb).
Most pcaps are mine, a few are from online sandboxes, and one is borrowed from malware.dontneedcoffee.com. That said, I can probably find the corresponding samples for all that have MD5 listed if you really need them. Search contagio, some are posted with the samples.
Each file has the following naming convention:
BIN [RTF, PDF] - the filetype of the dropper used, malware family name, MD5, and year+month of the malware analysis.
I will be adding more pcaps in the future. Please donate your pcaps from identified samples, I am sure many of you have.
Thank you
Download
 Download all together or separately.
Download all together or separately.All pcaps archives have the same password (same scheme), email me if you need it. I tried posting it without any passwords and pass infected but they get flagged as malware. Modern AV rips though zips and zips with the pass 'infected' with ease.
APT PCAPS
- 2012-12-31 BIN_Xinmic_8761F29AF1AE2D6FACD0AE5F487484A5-pcap
- 2013-09-08 BIN_TrojanPage_86893886C7CBC7310F7675F4EFDE0A29-pcap
- 2013-09-08 BIN_Darkcomet_DC98ABBA995771480AECF4769A88756E-pcap
- 2013-09-02 8202_tbd_ 6D2C12085F0018DAEB9C1A53E53FD4D1-pcap
- 2013-09-02 BIN_8202_6d2c12085f0018daeb9c1a53e53fd4d1-pcap
- 2013-09-02 BIN_Vidgrab_6fd868e68037040c94215566852230ab-pcap
- 2013-09-02 BIN_PlugX_2ff2d518313475a612f095dd863c8aea-pcap
- 2013-09-02 BIN_Taidoor_46ef9b0f1419e26f2f37d9d3495c499f-pcap
- 2013-09-02 BIN_Vidgrab_660709324acb88ef11f71782af28a1f0-pcap
- 2013-09-02 BIN_Gh0st-gif_f4d4076dff760eb92e4ae559c2dc4525-pcap.zip
- 2013-07-15 BIN_Taleret.E_5328cfcb46ef18ecf7ba0d21a7adc02c.pcap
- 2013-05-14 BIN_Mediana_0AE47E3261EA0A2DBCE471B28DFFE007_2012-10.pcap
- 2013-05-14 BIN_Hupigon_8F90057AB244BD8B612CD09F566EAC0C
- 2013-05-14 BIN_LetsGo_yahoosb_b21ba443726385c11802a8ad731771c0_2011-07-19
- 2013-05-13 BIN_IXESHE_0F88D9B0D237B5FCDC0F985A548254F2-2013-05-pcap
- 2013-05-06 BIN_DNSWatch_protux_4F8A44EF66384CCFAB737C8D7ADB4BB8_2012-11-pcap
- 2013-05-06 BIN_9002_D4ED654BCDA42576FDDFE03361608CAA_2013-01-30-pcap
- 2013-05-06 BIN_BIN_RssFeeder_68EE5FDA371E4AC48DAD7FCB2C94BAC7-2012-06-pcap (not a common name, see the traffic ssheet http://bit.ly/maltraffic )
- 2013-04-30 BIN_MSWab_Yayih_FD1BE09E499E8E380424B3835FC973A8_us-pcap
- 2013-04-29 BIN_LURK_AF4E8D4BE4481D0420CCF1C00792F484_20120-10-pcap
- 2013-04-29 BIN_XTremeRAT_DAEBFDED736903D234214ED4821EAF99_2013-04-13-pcap
- BIN_Enfal_Lurid_0fb1b0833f723682346041d72ed112f9_2013-01.pcap
- BIN_Gh0st_variant-v2010_B1D09374006E20FA795B2E70BF566C6D_2012-08.pcap
- BIN_Likseput_E019E37F19040059AB5662563F06B609_2012-10.pcap
- BIN_Nettravler_1f26e5f9b44c28b37b6cd13283838366.pcap
- BIN_Nettravler_DA5832657877514306EDD211DEF61AFE_2012-10.pcap
- BIN_Sanny-Daws_338D0B855421867732E05399A2D56670_2012-10.pcap
- BIN_Sofacy_a2a188cbf74c1be52681f998f8e9b6b5_2012-10.pcap
- BIN_Taidoor_40D79D1120638688AC7D9497CC819462_2012-10.pcap
- BIN_TrojanCookies_840BD11343D140916F45223BA05ABACB_2012_01.pcap
- PDF_CVE-2011-2462_Pdf_2011-12.pcap
- RTF_Mongall_Dropper_Cve-2012-0158_C6F01A6AD70DA7A554D48BDBF7C7E065_2013-01.pcap
- OSX_DocksterTrojan.pcap
CRIMEWARE PCAPS
- 2013-11-12_BIN_ChePro_2A5E5D3C536DA346849750A4B8C8613A-1.pcap
- 2013-10-15_BIN_cryptolocker_9CBB128E8211A7CD00729C159815CB1C.pcap
- 2013-09-20_BIN_Lader-dlGameoverZeus_12cfe1caa12991102d79a366d3aa79e9.pcap
- 2013-09-08 BIN_Tijcont_845B0945D5FE0E0AAA16234DC21484E0-pcap
- 2013-09-08 BIN_Kelihos_C94DC5C9BB7B99658C275B7337C64B33-pcap.zip
- 2013-08-19 BIN_Nitedrem_508af8c499102ad2ebc1a83fdbcefecb-pcap
- 2013-08-17 BIN_sality_CEAF4D9E1F408299144E75D7F29C1810-pcap
- 2013-08-15 BIN_torpigminiloader-pcap.zip
- 2013-13-08 EK_popads_109.236.80.170_2013-08-13.pcap
- 2013-11-08 BIN_Alinav5.3_4C754150639AA3A86CA4D6B6342820BE.pcap
- 2013-08-08 BIN_BitcoinMiner_F865C199024105A2FFDF5FA98F391D74-pcap
- 2013-08-07 BIN_ZeroAccess_Sirefef_C2A9CCC8C6A6DF1CA1725F955F991940_2013-08-pcap
- 2013-07-05 BIN_Kuluoz-Asprox_9F842AD20C50AD1AAB41F20B321BF84B
- 2013-05-31 Wordpress-Mutopy_Symmi_20A6EBF61243B760DD65F897236B6AD3-2pcap.pcap
- 2013-05-15 BIN_Zeus_b1551c676a54e9127cd0e7ea283b92cc-2012-04.pcap
- 2013-05-15 BIN_Gypthoy_3EE49121300384FF3C82EB9A1F06F288-2013-05.pcap
- 2013-05-12 BIN_PassAlert_B4A1368515C6C39ACEF63A4BC368EDB2-2013-05-13
- 2013-05-12 BIN_HorstProxy_EFE5529D697174914938F4ABF115F762-2013-05-13-pcap
- 2013-05-12 BIN_Bitcoinminer_12E717293715939C5196E604591A97DF-2013-05-12-pcap
- 2013-05-07 BIN_ZeroAccess_Sirefef_29A35124ABEAD63CD8DB2BBB469CBC7A_2013-05-pcapc
- 2013-05-05 BIN_PowerLoader_4497A231DA9BD0EEA327DDEC4B31DA12_2013-05-pcap
- 2013-05-05 BIN_GameThief_ECBA0FEB36F9EF975EE96D1694C8164C_2013-03-pcap
- 2013-05-05 BIN_PowerLoader_4497A231DA9BD0EEA327DDEC4B31DA12_2013-05-pcap
- 2013-04-27 EK_BIN_Blackhole_leadingto_Medfos_0512E73000BCCCE5AFD2E9329972208A_2013-04-pcap
- 2013-04-26 -- BIN_Citadel_3D6046E1218FB525805E5D8FDC605361-2013-04-samp
- BIN_CitadelPacked_2012-05.pcap
- BIN_CitadelUnpacked_2012-05.pcap
- BIN_Cutwail_284Fb18Fab33C93Bc69Ce392D08Fd250_2012-10.pcap
- BIN_Darkmegi_2012-04.pcap
- BIN_DarknessDDoS_v8g_F03Bc8Dcc090607F38Ffb3A36Ccacf48_2011-01.pcap-
- BIN_dirtjumper_2011-10.pcap
- BIN_DNSChanger_2011-12.pcap
- BIN_Drowor_worm_0f015bb8e2f93fd7076f8d178df2450d_2013-04.pcap
- BIN_Googledocs_macadocs_2012-12.pcap
- BIN_Imaut_823e9bab188ad8cb30c14adc7e67066d.pcap
- BIN_IRCbot_c6716a417f82ccedf0f860b735ac0187_2013-04.pcap
- BIN_Kelihos_aka_Nap_0feaaa4adc31728e54b006ab9a7e6afa.pcap
- BIN_LoadMoney_MailRu_dl_4e801b46068b31b82dac65885a58ed9e_2013-04 .pcap
- BIN_purplehaze-2012-01.pcap
- BIN_ponyloader_470a6f47de43eff307a02f53db134289.pcap
- BIN_Ramnitpcap_2012-01.pcap
- BIN_Reedum_0ca4f93a848cf01348336a8c6ff22daf_2013-03.pcap
- BIN_SpyEye_2010-02.pcap
- BIN_Stabuniq_F31B797831B36A4877AA0FD173A7A4A2_2012-12.pcap
- BIN_Tbot_23AAB9C1C462F3FDFDDD98181E963230_2012-12.pcap
- BIN_Tbot_2E1814CCCF0C3BB2CC32E0A0671C0891_2012-12.pcap
- BIN_Tbot_5375FB5E867680FFB8E72D29DB9ABBD5_2012-12.pcap
- BIN_Tbot_A0552D1BC1A4897141CFA56F75C04857_2012-12.pcap
- BIN_Tbot_FC7C3E087789824F34A9309DA2388CE5_2012-12.pcap
- BIN_Tinba_2012-06.pcap
- BIN_Vobfus_634AA845F5B0B519B6D8A8670B994906_2012-12.pcap
- BIN_Xpaj_2012-05.pcap
- BIN_ZeroAccess_3169969E91F5FE5446909BBAB6E14D5D_2012-10.pcap
- BIN_ZeusGameover_2012-02.pcap
- BIN_Zeus_2010-12.pcap
- EK_Blackholev1_2012-03.pcap
- EK_Blackholev1_2012-08.pcap
- EK_Blackholev2_2012-09.pcap
- EK_Blackhole_Java_CVE-2012-4681_2012-08.pcap
- EK_Phoenix_2012-04.pcap
- EK_Smokekt150(Malwaredontneedcoffee)_2012-09.pcap - credit malware.dontneedcoffee.com
More info
WHO IS ETHICAL HACKER
Who is hacker?
A hacker is a Creative person and a creative Programmer,who have knowledge about Networking,Operating system,hacking & a best creative social engineer who control anyone's mind he is also a knowledgeable person.
A hacker is a Creative person and a creative Programmer,who have knowledge about Networking,Operating system,hacking & a best creative social engineer who control anyone's mind he is also a knowledgeable person.
Hacker are the problem solver and tool builder.
OR
A hacker is an individual who uses computer, networking and other skills to overcome a technical problem but it often refers to a person who uses his or her abilities to gain unauthorized access to system or networks in order to commit crimes.
Related links
CEH: Gathering Host And Network Information | Scanning
Scanning
It is important that the information-gathering stage be as complete as possible to identify the best location and targets to scan. After the completion of footprinting and information gathering methodologies, scanning is performed.During scanning, the hacker has vision to get information about network an hosts which are connected to that network that can help hackers to determine which type of exploit to use in hacking a system precisely. Information such as an IP addresses, operating system, services, and installed applications.
Scanning is the methodology used to detect the system that are alive and respond on the network or not. Ethical hackers use these type of scanning to identify the IP address of target system. Scanning is also used to determine the availability of the system whether it is connected to the network or not.
Types Of Scanning
| Network Scanning | Identifies IP addresses on a given network or subnet |
| Port Scanning | Determines open, close, filtered and unfiltered ports and services |
| Vulnerability Scanner | Detect the vulnerability on the target system |
Port Scanning
Port scanning is the process of identifying open and available TCP/IP ports on a system. Port-scanning tools enable a hacker to learn about the services available on a given system. Each service or application on a machine is associated with a well-known port number. Port Numbers are divided into three ranges:- Well-Known Ports: 0-1023
- Registered Ports: 1024-49151
- Dynamic Ports: 49152-6553
Network Scanning
Network scanning is performed for the detection of active hosts on a network either you wanna attack them or as a network administrator. Network-scanning tools attempt to identify all the live or responding hosts on the network and their corresponding IP addresses. Hosts are identified by their individual IP addresses.Vulnerability Scanning
This methodology is used to detect vulnerabilities of computer systems on a network. A vulnerability scanner typically identifies the operating system and version number, including applications that are installed. After that the scanner will try to detect vulnerabilities and weakness in the operating system. During the later attack phase, a hacker can exploit those weaknesses in order to gain access to the system. Moreover, the vulnerability scanner can be detected as well, because the scanner must interact over the network with target machine.The CEH Scanning Methodology
As a CEH, you should understand the methodology about scanning presented in the figure below. Because this is the actual need of hackers to perform further attacks after the information about network and hosts which are connected to the network. It detects the vulnerabilities in the system bu which hackers can be accessible to that system by exploitation of that vulnerabilities.Related news
Networking | Routing And Switching | Tutorial 4 | 2018
Welcome to my 4th new tutorial of the series of networking. In this blog you'll the content about network switches. You'll learn about how to make a communication successful and secure in the same network (LAN) by using STP. As Spanning tree protocol (STP) we used in multi-switched networks. Why we use this protocol in multi-switched network etc.
What is Switch?
A switch is an intelligent device used to connect multiple devices within the same network. The intelligence of is that it requires Media Access Control (MAC) address for communication and doesn't allow broadcast. Let's understand the whole thing by a little example, consider there is a network having 3 end devices name Device-A, Device-B,Device-C connected with each other respectively with the help of switch. When a Device-A sends data to Device-C so that data will only forwarded by switch to Device-C not to Device-B.What is Media Access Control (MAC) address?
A Media Access Control (MAC) address is 48-bit unique physical address given to network interface controller (NIC) or network adapter, for communication within the same network which is given by its manufacturer. It is made up of hexadecimal numbers like a1:b1:cc:ac:2e:f1.What is STP?
STP stands for Spanning tree protocol which is basically used in bridge and switches to prevent loops when you have a redundant links in the Ethernet networks. If the loop is present in the Ethernet network so the whole network will suffer because there will MAC instability in the MAC table, duplicate frames generation and so on. Let's move to the video for further detail.
More info
Jun 10, 2020
How To Recover Files That Are Deleted From Recycle Bin

How To Recover Files That Are Deleted From Recycle Bin
How To Recover Files That Are Deleted From Recycle Bin
Well, Windows users have a bad habit of removing files from recycle bin. Deleting useless files from Recycle Bin helps a user to save some storage space which can improve the speed of a computer. However, Windows users do that more frequently and later regret. Actually, Recycle Bin is a place from where we can get back our deleted files and folders.
Sometimes, we accidentally delete our important files and folders and due to some reason we lose them from Recycle bin too! At that time, we search for recovery methods. Well, there are many methods available over the web which can help you to recover deleted files from computer, but, when it comes to reliability, nothing can beat EaseUS.
What Is EaseUS Data Recovery Wizard?
EaseUS is one of the leading software providers which is known for its data recovery programme. EaseUS offers some free data recovery software that can help you to recover deleted, formatted or lost data from PC, laptop or removable device easily and quickly.
One of the best thing about EaseUS is that it provides tools for recycle bin recovery which can help you to get back files that you have deleted from the Recycle bin itself. EaseUS Data Recovery Wizard free can easily recover lost files, pictures, documents, videos and more from deleting, formatting, partition loss, OS crash, virus attack and other data loss cases.
How To Recover Deleted Files?
If you are struggling to get back your lost data files, then here is an easy data recovery method which will help you to get back deleted files on your computer. Below, we are going to share a mini guide on how to use EaseUS Recycle Bin Recovery to get back your deleted data.
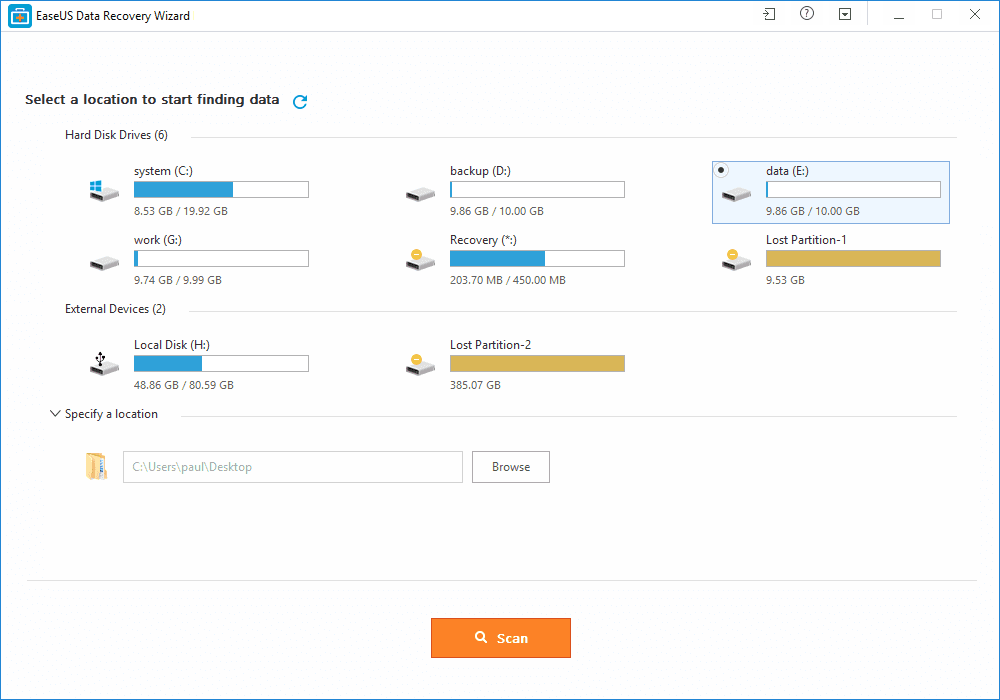
Step 1. First of all, you need to download and install EaseUS Data Recovery Wizard on your Windows computer and then launch it normally. You need to select the location where you want to scan and then click on 'Scan'
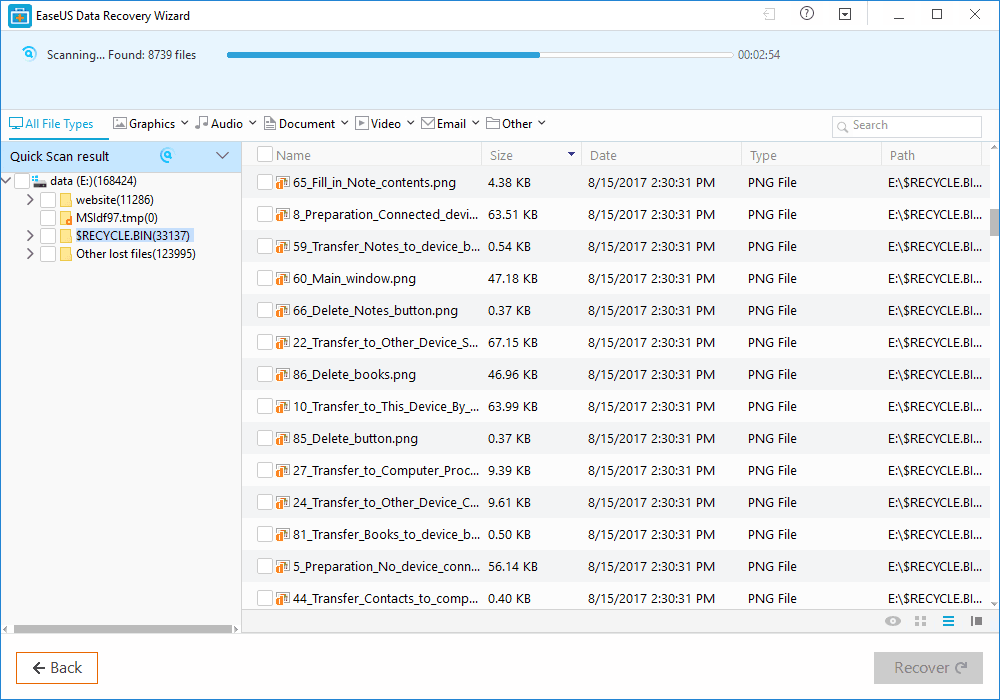
Step 2. Now, wait for few minutes until the tool finishes scanning your drive. The tool search for files that got deleted or cleaned from the Recycle Bin.
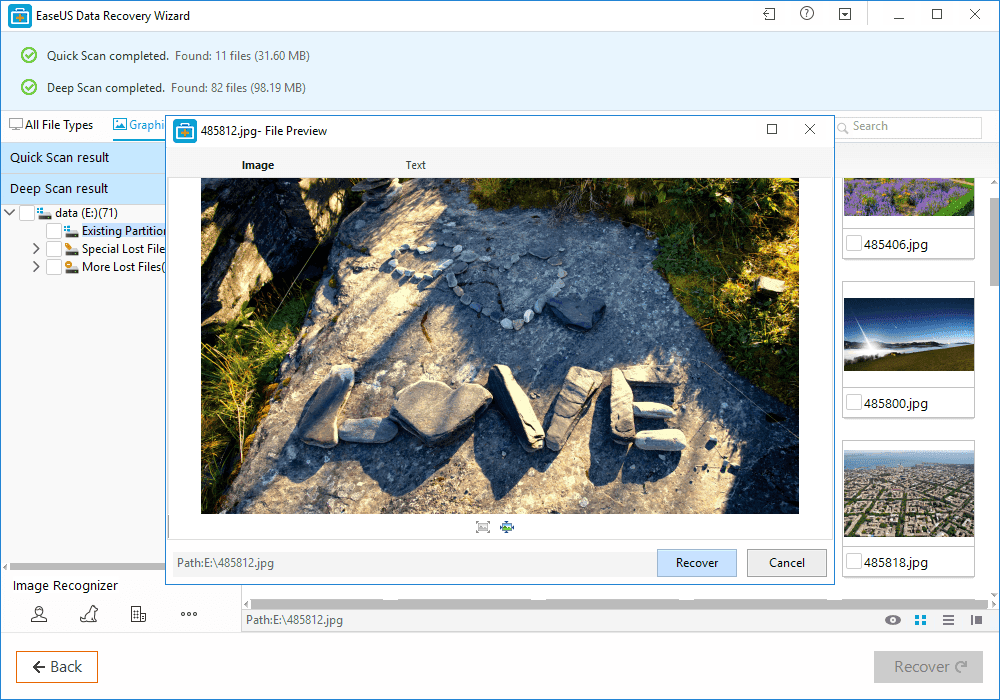
Step 3. Now it will show you files that you can recover. Here you need to click on the file which you want to recover and click on 'Recover'
That's it, you are done! This is how you can use EaseUS data recovery to get back your deleted files on your computer.
Benefits of EaseUS Data Recovery
Well, the data recovery tool provided by EaseUS comes with many benefits. It can not only recover accidentally deleted files, but it can also recover data in case of Virus Attacks, Hard Disk Damage, OS Crash etc.
You can also use this awesome data recovery wizard to recover deleted files from External Disk, USB Drive, Camcorder, Mobile Devices, Zip Drive, iPod, Music Player and more.
Overall, this is one of the best data recovery tools you can have on your Windows computer. EaseUS Data Recovery also has a free version with restricted features. Overall, this is a stress-free solution to get back your deleted files
Continue reading
Subscribe to:
Posts (Atom)